The protection of your own machines is never enough. Whether or not you’re running a business and even in the home, all layers of protection are important to maintain all of your computerized details safe. Online, all the company procedures are taken outside the personal computer, even in your own home, consumer banking functions, transactions, receipt of repayments, and much more.
As a result our sensitive information and facts prone to getting hijacked and used in indiscriminate approaches. The thievery of bookkeeping and personality information and facts to help make prohibited purchases inside your label is extremely typical, so trying to keep your PC shielded is essential.
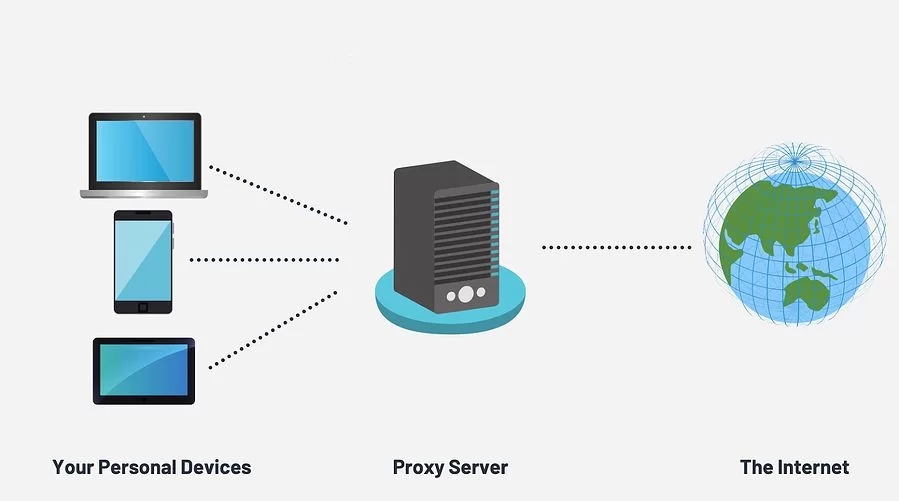
The usage of residential and organization proxies is a great way to produce a defensive obstacle in between your terminal and also the open public network. By doing this, every one of the data exchanged using the assistance providers’ machines depart the proxies.
The operations is fairly basic. When you enter a web page, you will be making a demand from the laptop or computer that trips to the web server where it will be served, along with a reaction will create to satisfy it. This response calls for sensitive information and facts to be granted, by way of example, your Ip address, spot, etc.
For that reason, this data is going to be traveling without protection through the system, which makes it vulnerable to intercept.
A good choice is mobile proxies.
With the mobile proxies, you could be quiet since your pc will only achieve the mobile proxies where it will probably be encrypted, and a ask for will problem with the proxy’s details, as well as the details of the pc and every little thing.
It would conceal. This way, if the details are intercepted, they will likely only get the IP and site of the proxy utilized. Become a mobile phone proxy. It will be extremely difficult to follow you and your pc customers.
Apply private proxies for your organization or business office
With this type of intermediary, you are able to protect each of the sensitive info saved in your company’s terminals. In addition, you are going to maintain a lot more thorough control over the action provided by these computer systems.
In this way, you will be able to manage the movement of data that goes in leaving your organization, obstructing those suspicious impulses even finding some abnormal behavior within the computer customers.